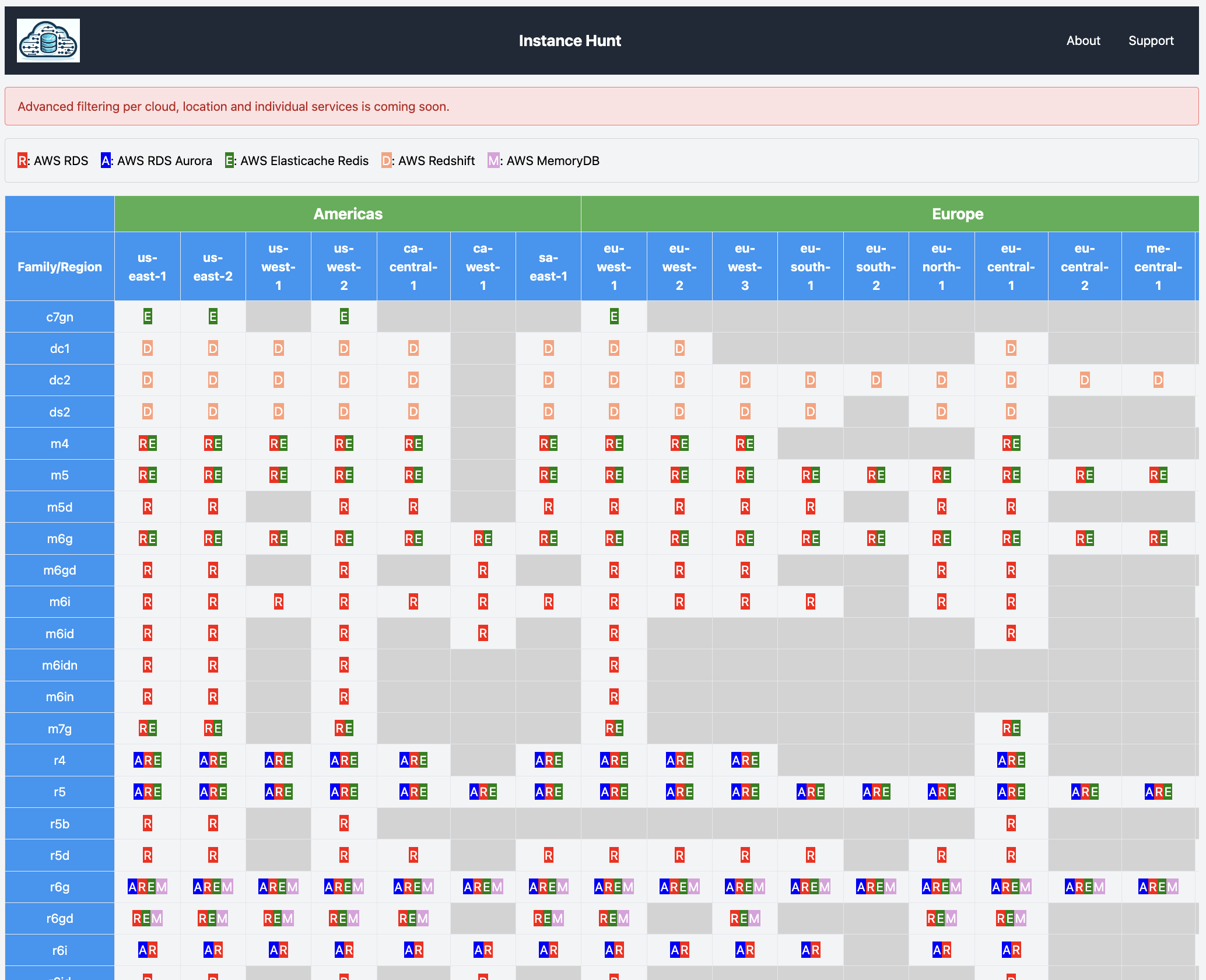
We know that SQL statement compatibility can change with major database version upgrades and that you should adequately test for them. But what about minor version upgrades?
It is dangerous to assume that your existing SQL statements work with a minor update, especially when using an augmented version of an open-source database such as a cloud provider that may not be as transparent about all changes.
While I have always found reading the release notes an important step in architectural principles over the decades, many organizations skip over this principle and get caught off guard when there are no dedicated DBAs and architects in the engineering workforce.
Real-world examples of minor version upgrade issues
Here are two real-world situations common in the AWS RDS ecosystem using MySQL.
- You are an organization that uses RDS Aurora MySQL for its production systems, and you upgrade one minor version at a time. A diligent approach is to be one minor version behind unless a known bug is fixed in a newer version you depend on.
- You are an organization that, to save costs with a comprehensive engineering team, uses AWS RDS MySQL (not Aurora) for developers and some testing environments.
I’ve simplified a real-world example to a simple SQL statement and combined these two separate use cases into one simulated situation for demonstration purposes.
mysql> SELECT content_type FROM reserved2; Empty set (0.00 sec) mysql> SELECT VERSION(), @@aurora_version; +-----------+------------------+ | VERSION() | @@aurora_version | +-----------+------------------+ | 8.0.28 | 3.04.2 | +-----------+------------------+ mysql> SELECT VERSION(); +-----------+ | VERSION() | +-----------+ | 8.0.34 | +-----------+ 1 row in set (0.00 sec)
This is a simple enough query, this runs in AWS RDS Aurora MySQL 3.04.02 (which is the present Aurora MySQL long-term support (LTS) release). This is based on MySQL 8.0.28 which is FWIW not a supported AWS RDS MySQL version anymore, the minimum is now 8.0.32 (Supported MySQL minor versions on Amazon RDS).
It runs in AWS RDS MySQL 8.0.34 which is for example what version your developer setup is.
An AWS RDS MySQL Aurora minor version upgrade
You decide to upgrade from Aurora 3.04.x/3.05.x to 3.06.x. This Aurora version is actually based on MySQL 8.0.34 (the version you just tested in RDS). Without adequate due diligence you roll out to production only to find after the fact that this SQL statement (realize this is one simplified example for demonstrate purposes) now breaks for no apparent reason.
mysql> select content_type from reserved2; ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'content_type from reserved2' at line 1 mysql> SELECT VERSION(), @@aurora_version; +-----------+------------------+ | VERSION() | @@aurora_version | +-----------+------------------+ | 8.0.34 | 3.06.0 | +-----------+------------------+
Now, you need to investigate the problem, which can take hours, even days of resource time, and a lot of shaking heads to realize it has nothing to do with your application code but to do with the minor version upgrade. Which you simply cannot roll back. See Risks from auto upgrades with managed database services for some interesting facts.
Wait, what just happened?
If you performed this upgrade to the latest AWS RDS Aurora MySQL 3.06.0 version sometime after the release on 3/7/24 and before 6/4/24, a 3-month period, you are left with one choice. You have to make application code changes to address the breakage.
How many man-hours/man-days does this take? If you upgraded to this version in the past two weeks, technically you have a second choice. You can go to the most current version, 3.07.0, but you have already spent time in testing and deploying 3.06.0, which you need to re-test, then rollout in non-production accounts and then rollout to production. How many man-days of work is this?
It may be hard to justify the cost of automated testing until you uncover a situation like this one; however, it can easily be avoided in the future.
So why did this happen?
Lets look deeper are the fine-print
RDS Aurora MySQL 3.06.0
Aurora MySQL version 3.06.0 supports Amazon Bedrock integration and introduces the new reserved keywords accept, aws_bedrock_invoke_model, aws_sagemaker_invoke_endpoint, content_type, and timeout_ms. Check the object definitions for the usage of the new reserved keywords before upgrading to version 3.06.0. To mitigate the conflict with the new reserved keywords, quote the reserved keywords used in the object definitions. For more information on the Amazon Bedrock integration and handling the reserved keywords, see What is Amazon Bedrock? in the Amazon Aurora User Guide. For additional information, see Keywords and Reserved Words, The INFORMATION_SCHEMA KEYWORDS Table, and Schema Object Names in the MySQL documentation.
From AWS RDS Aurora MySQL 3.06.0 release notes (3/7/24).
While less likely you would name a column aws_bedrock_invoke_model, column names of content_type and timeout_ms are common words.
RDS Aurora MySQL 3.07.0
Aurora MySQL version
3.06.0added support for Amazon Bedrock integration. As part of this, new reserved keywords (accept, aws_bedrock_invoke_model, aws_sagemaker_invoke_endpoint, content_type, and timeout_ms) were added. In Aurora MySQL version3.07.0, these keywords have been changed to nonreserved keywords, which are permitted as identifiers without quoting. For more information on how MySQL handles reserved and nonreserved keywords, see Keywords and reserved words in the MySQL documentation.
From AWS RDS Aurora MySQL 3.07.0 release notes (6/4/24). Clearly someone at AWS saw the breaking changes and it was reverted. While it’s possible many customers may not need to catch this situation, this is one specific use case.
Conclusion
The moral of the database story here is Be Prepared.
You should always be prepared for future breaking compatibility. You should test with a regular software upgrade cadence and leverage automation as much as possible.
Next BaseLine is a software product that automates testing for many use cases, including this simple SQL compatibility issue. By adding to your CI/CD pipeline can help identify and risk in all SQL database access, including new engineering software releases or infrastructure updates. This product can be implemented in a few hours, and cost significantly less than the large amount of time lost with this one realistic situation.
Footnote
This example was not uncovered from a customer situation. It was uncovered and used as a demonstration because I read the release notes.
Test Case
SELECT VERSION();
SELECT VERSION(), @@aurora_version; /* No way to comment out the !Aurora example */
CREATE SCHEMA IF NOT EXISTS test;
USE test;
CREATE TABLE reserved1(id INT UNSIGNED NOT NULL AUTO_INCREMENT PRIMARY KEY, accept CHAR(1) NOT NULL DEFAULT 'N');
CREATE TABLE reserved2(id INT UNSIGNED NOT NULL AUTO_INCREMENT PRIMARY KEY, content_type VARCHAR(10) NULL DEFAULT 'text/plain');
CREATE TABLE reserved3(id INT UNSIGNED NOT NULL AUTO_INCREMENT PRIMARY KEY, timeout_ms INT UNSIGNED NOT NULL);
SELECT accept FROM reserved1;
SELECT content_type FROM reserved2;
SELECT timeout_ms FROM reserved3;

 Image generated by ChatGPT. Mistakes left as a reminder genAI is not there yet for text.
Image generated by ChatGPT. Mistakes left as a reminder genAI is not there yet for text.