I recently became aware of WeSQL. A MySQL-compatible database that separates compute and storage, using S3 as the storage layer. The product uses a columnar format by default which is significantly more space-efficient than InnoDB.
WeSQL introduces a new storage engine called SmartEngine using a LSM-tree-based structure that is ideal for a storage bucket implementation, and documentation shows the implementation of raft replication to combat latency concerns. There is a lot more information to review, the serverless architecture and WeScale, a database proxy and resource manager.
It was very easy to take it for an initial spin using a docker container and an AWS S3 bucket. I would really like to try CloudFlare R2 which implements the S3 API.
Under the covers there are over 180 new variables comprising 83 for the smartengine, 57 for raft, and 22 for objectstore and more. This implies a lot of tunable options and a lot of complexity to optimize for a variety of workloads using the 79 new status variables.
I was able to launch a demo and confirm
mysql> SELECT VERSION(); +-----------+ | VERSION() | +-----------+ | 8.0.35 | +-----------+ 1 row in set (0.01 sec) mysql> SELECT @@wesql_version; +-----------------+ | @@wesql_version | +-----------------+ | 0.1.0 | +-----------------+ 1 row in set (0.00 sec)
One of my early tests showed that it does not support FOREIGN KEYS, which is not a major concern.
ERROR 1235 (42000) at line 10: SE currently doesn't support foreign key constraints
I did have some subsequent issues with the current docs version 8.0.35-0.1.0_beta1.37 and I did revert to a prior version from docs earlier this week 8.0.35-0.1.0_beta1.gedaf338.36. Given it’s a very new product I am sure there is a lot of ongoing development.
This is just a quick introduction but it’s a definitely a different architecture in the RDBMS landscape for MySQL compatibility. I hope to run some more tests using the provided sysbench use cases and my own workloads to delve under the covers more.
New Variables
branch_objectstore_id clone_autotune_concurrency clone_block_ddl clone_buffer_size clone_ddl_timeout clone_delay_after_data_drop clone_donor_timeout_after_network_failure clone_enable_compression clone_max_concurrency clone_max_data_bandwidth clone_max_network_bandwidth clone_ssl_ca clone_ssl_cert clone_ssl_key clone_valid_donor_list initialize_branch_objectstore_id initialize_from_objectstore initialize_objectstore_bucket initialize_objectstore_endpoint initialize_objectstore_provider initialize_objectstore_region initialize_objectstore_use_https initialize_repo_objectstore_id initialize_smartengine_objectstore_data objectstore_bucket objectstore_endpoint objectstore_mtr_test_bucket_dir objectstore_provider objectstore_region objectstore_use_https raft_replication_allow_no_valid_entry raft_replication_appliedindex_force_delay raft_replication_archive_log_bin_index raft_replication_archive_recovery raft_replication_archive_recovery_stop_datetime raft_replication_auto_leader_transfer raft_replication_auto_leader_transfer_check_seconds raft_replication_auto_reset_match_index raft_replication_check_commit_index_interval raft_replication_checksum raft_replication_cluseter_info_on_objectstore raft_replication_cluster_id raft_replication_cluster_info raft_replication_configure_change_timeout raft_replication_current_term raft_replication_disable_election raft_replication_disable_fifo_cache raft_replication_dynamic_easyindex raft_replication_election_timeout raft_replication_flow_control raft_replication_force_change_meta raft_replication_force_recover_index raft_replication_force_reset_meta raft_replication_force_single_mode raft_replication_force_sync_epoch_diff raft_replication_heartbeat_thread_cnt raft_replication_io_thread_cnt raft_replication_large_batch_ratio raft_replication_large_event_split_size raft_replication_large_trx raft_replication_learner_heartbeat raft_replication_learner_node raft_replication_learner_pipelining raft_replication_learner_timeout raft_replication_log_cache_size raft_replication_log_level raft_replication_log_type_node raft_replication_max_delay_index raft_replication_max_log_size raft_replication_max_packet_size raft_replication_min_delay_index raft_replication_mts_recover_use_index raft_replication_new_follower_threshold raft_replication_optimistic_heartbeat raft_replication_pipelining_timeout raft_replication_prefetch_cache_size raft_replication_prefetch_wakeup_ratio raft_replication_prefetch_window_size raft_replication_purged_gtid raft_replication_recover_backup raft_replication_recover_new_cluster raft_replication_reset_prefetch_cache raft_replication_send_timeout raft_replication_start_index raft_replication_sync_follower_meta_interva raft_replication_with_cache_log raft_replication_worker_thread_cnt recovery_snapshot_from_objectstore recovery_snapshot_only recovery_snapshot_timestamp recovery_snapshot_tmpdir repo_objectstore_id server_id_on_objectstore serverless smartengine_auto_shrink_enabled smartengine_auto_shrink_schedule_interval smartengine_batch_group_max_group_size smartengine_batch_group_max_leader_wait_time_us smartengine_batch_group_slot_array_size smartengine_block_cache_size smartengine_block_size smartengine_bottommost_level smartengine_bulk_load_size smartengine_compact smartengine_compaction_delete_percent smartengine_compaction_task_extents_limit smartengine_compaction_threads smartengine_compression_options smartengine_compression_per_level smartengine_concurrent_writable_file_buffer_num smartengine_concurrent_writable_file_buffer_switch_limit smartengine_concurrent_writable_file_single_buffer_size smartengine_data_dir smartengine_deadlock_detect smartengine_disable_auto_compactions smartengine_disable_instant_ddl smartengine_disable_online_ddl smartengine_disable_parallel_ddl smartengine_dump_memtable_limit_size smartengine_enable_2pc smartengine_estimate_cost_depth smartengine_flush_delete_percent smartengine_flush_delete_percent_trigger smartengine_flush_delete_record_trigger smartengine_flush_log_at_trx_commit smartengine_flush_memtable smartengine_flush_threads smartengine_hotbackup smartengine_idle_tasks_schedule_time smartengine_level0_file_num_compaction_trigger smartengine_level0_layer_num_compaction_trigger smartengine_level1_extents_major_compaction_trigger smartengine_level2_usage_percent smartengine_level_compaction_dynamic_level_bytes smartengine_lock_scanned_rows smartengine_lock_wait_timeout smartengine_master_thread_compaction_enabled smartengine_master_thread_monitor_interval_ms smartengine_max_background_dumps smartengine_max_free_extent_percent smartengine_max_row_locks smartengine_max_shrink_extent_count smartengine_max_write_buffer_number_to_maintain smartengine_memtable_size smartengine_min_write_buffer_number_to_merge smartengine_mutex_backtrace_threshold_ns smartengine_parallel_flush_log smartengine_parallel_read_threads smartengine_parallel_recovery_thread_num smartengine_parallel_wal_recovery smartengine_pause_background_work smartengine_persistent_cache_dir smartengine_persistent_cache_mode smartengine_persistent_cache_size smartengine_purge_invalid_subtable_bg smartengine_query_trace_print_slow smartengine_query_trace_sum smartengine_query_trace_threshold_time smartengine_rate_limiter_bytes_per_sec smartengine_reset_pending_shrink smartengine_row_cache_size smartengine_scan_add_blocks_limit smartengine_shrink_allocate_interval smartengine_shrink_table_space smartengine_sort_buffer_size smartengine_stats_dump_period_sec smartengine_strict_collation_check smartengine_strict_collation_exceptions smartengine_table_cache_numshardbits smartengine_table_cache_size smartengine_total_max_shrink_extent_count smartengine_total_memtable_size smartengine_total_wal_size smartengine_unsafe_for_binlog smartengine_wal_dir smartengine_wal_recovery_mode smartengine_write_disable_wal snapshot_archive snapshot_archive_dir snapshot_archive_expire_auto_purge snapshot_archive_expire_seconds snapshot_archive_innodb_tar_mode snapshot_archive_on_objectstore snapshot_archive_period snapshot_archive_smartengine_backup_checkpoint snapshot_archive_smartengine_tar_mode table_on_objectstore wesql_version
New Status
Com_show_consensuslogs
Com_raft_replication_start
Com_raft_replication_stop
Com_native_admin_proc
Com_native_trans_proc
Com_show_consensuslog_events
Smartengine_block_cache_miss
Smartengine_block_cache_hit
Smartengine_block_cache_add
Smartengine_block_cache_index_miss
Smartengine_block_cache_index_hit
Smartengine_block_cache_filter_miss
Smartengine_block_cache_filter_hit
Smartengine_block_cache_data_miss
Smartengine_block_cache_data_hit
Smartengine_row_cache_add
Smartengine_row_cache_hit
Smartengine_row_cache_miss
Smartengine_memtable_hit
Smartengine_memtable_miss
Smartengine_number_keys_written
Smartengine_number_keys_read
Smartengine_number_keys_updated
Smartengine_bytes_written
Smartengine_bytes_read
Smartengine_block_cachecompressed_miss
Smartengine_block_cachecompressed_hit
Smartengine_wal_synced
Smartengine_wal_bytes
Smartengine_write_self
Smartengine_write_other
Smartengine_write_wal
Smartengine_number_superversion_acquires
Smartengine_number_superversion_releases
Smartengine_number_superversion_cleanups
Smartengine_number_block_not_compressed
Smartengine_snapshot_conflict_errors
Smartengine_wal_group_syncs
Smartengine_rows_deleted
Smartengine_rows_inserted
Smartengine_rows_updated
Smartengine_rows_read
Smartengine_system_rows_deleted
Smartengine_system_rows_inserted
Smartengine_system_rows_updated
Smartengine_system_rows_read
Smartengine_max_level0_layers
Smartengine_max_imm_numbers
Smartengine_max_level0_fragmentation_rate
Smartengine_max_level1_fragmentation_rate
Smartengine_max_level2_fragmentation_rate
Smartengine_max_level0_delete_percent
Smartengine_max_level1_delete_percent
Smartengine_max_level2_delete_percent
Smartengine_all_flush_megabytes
Smartengine_all_compaction_megabytes
Smartengine_top1_subtable_size
Smartengine_top2_subtable_size
Smartengine_top3_subtable_size
Smartengine_top1_mod_mem_info
Smartengine_top2_mod_mem_info
Smartengine_top3_mod_mem_info
Smartengine_global_external_fragmentation_rate
Smartengine_write_transaction_count
Smartengine_pipeline_group_count
Smartengine_pipeline_group_wait_timeout_count
Smartengine_pipeline_copy_log_size
Smartengine_pipeline_copy_log_count
Smartengine_pipeline_flush_log_size
Smartengine_pipeline_flush_log_count
Smartengine_pipeline_flush_log_sync_count
Smartengine_pipeline_flush_log_not_sync_count
Com_show_consensuslogs Com_raft_replication_start Com_raft_replication_stop Com_native_admin_proc Com_native_trans_proc Com_show_consensuslog_events Smartengine_block_cache_miss Smartengine_block_cache_hit Smartengine_block_cache_add Smartengine_block_cache_index_miss Smartengine_block_cache_index_hit Smartengine_block_cache_filter_miss Smartengine_block_cache_filter_hit Smartengine_block_cache_data_miss Smartengine_block_cache_data_hit Smartengine_row_cache_add Smartengine_row_cache_hit Smartengine_row_cache_miss Smartengine_memtable_hit Smartengine_memtable_miss Smartengine_number_keys_written Smartengine_number_keys_read Smartengine_number_keys_updated Smartengine_bytes_written Smartengine_bytes_read Smartengine_block_cachecompressed_miss Smartengine_block_cachecompressed_hit Smartengine_wal_synced Smartengine_wal_bytes Smartengine_write_self Smartengine_write_other Smartengine_write_wal Smartengine_number_superversion_acquires Smartengine_number_superversion_releases Smartengine_number_superversion_cleanups Smartengine_number_block_not_compressed Smartengine_snapshot_conflict_errors Smartengine_wal_group_syncs Smartengine_rows_deleted Smartengine_rows_inserted Smartengine_rows_updated Smartengine_rows_read Smartengine_system_rows_deleted Smartengine_system_rows_inserted Smartengine_system_rows_updated Smartengine_system_rows_read Smartengine_max_level0_layers Smartengine_max_imm_numbers Smartengine_max_level0_fragmentation_rate Smartengine_max_level1_fragmentation_rate Smartengine_max_level2_fragmentation_rate Smartengine_max_level0_delete_percent Smartengine_max_level1_delete_percent Smartengine_max_level2_delete_percent Smartengine_all_flush_megabytes Smartengine_all_compaction_megabytes Smartengine_top1_subtable_size Smartengine_top2_subtable_size Smartengine_top3_subtable_size Smartengine_top1_mod_mem_info Smartengine_top2_mod_mem_info Smartengine_top3_mod_mem_info Smartengine_global_external_fragmentation_rate Smartengine_write_transaction_count Smartengine_pipeline_group_count Smartengine_pipeline_group_wait_timeout_count Smartengine_pipeline_copy_log_size Smartengine_pipeline_copy_log_count Smartengine_pipeline_flush_log_size Smartengine_pipeline_flush_log_count Smartengine_pipeline_flush_log_sync_count Smartengine_pipeline_flush_log_not_sync_count

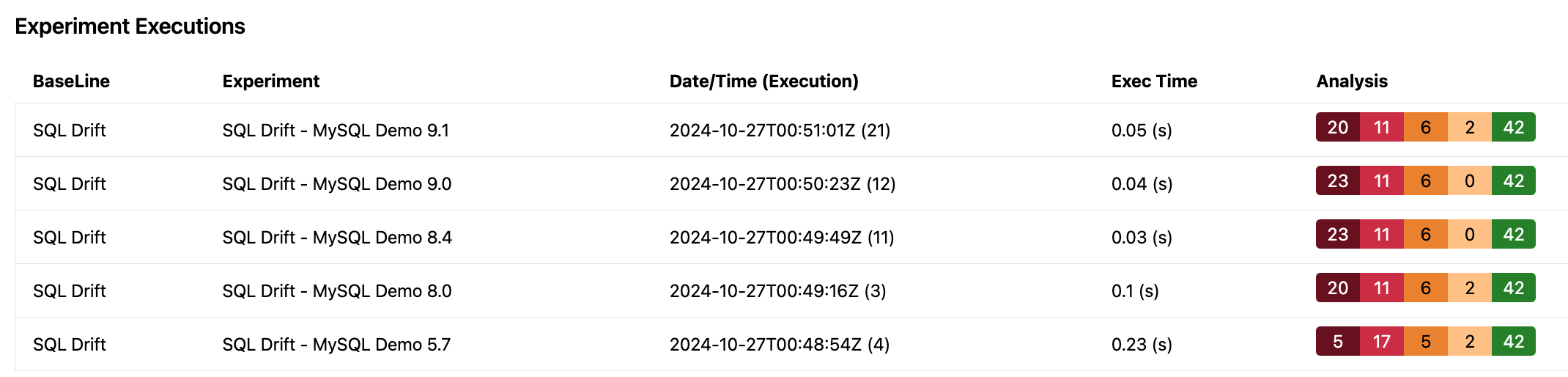
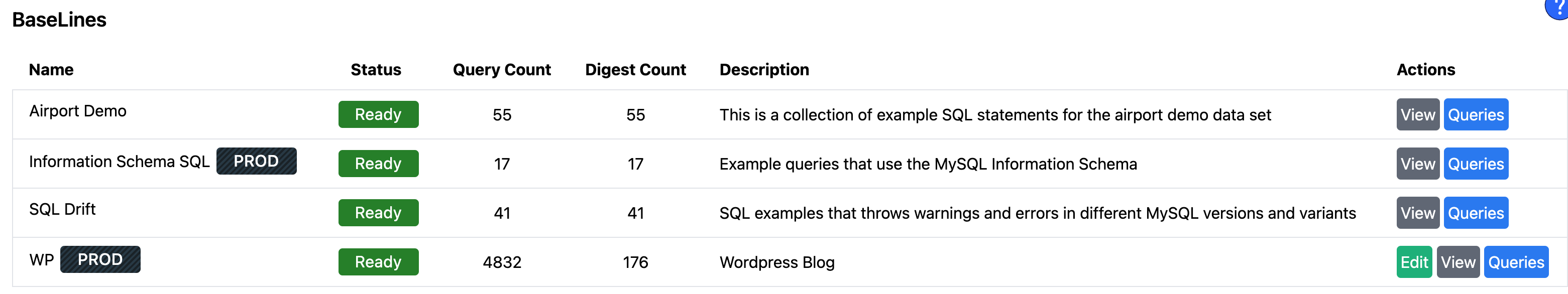
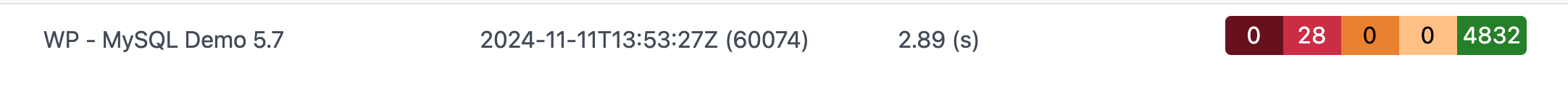


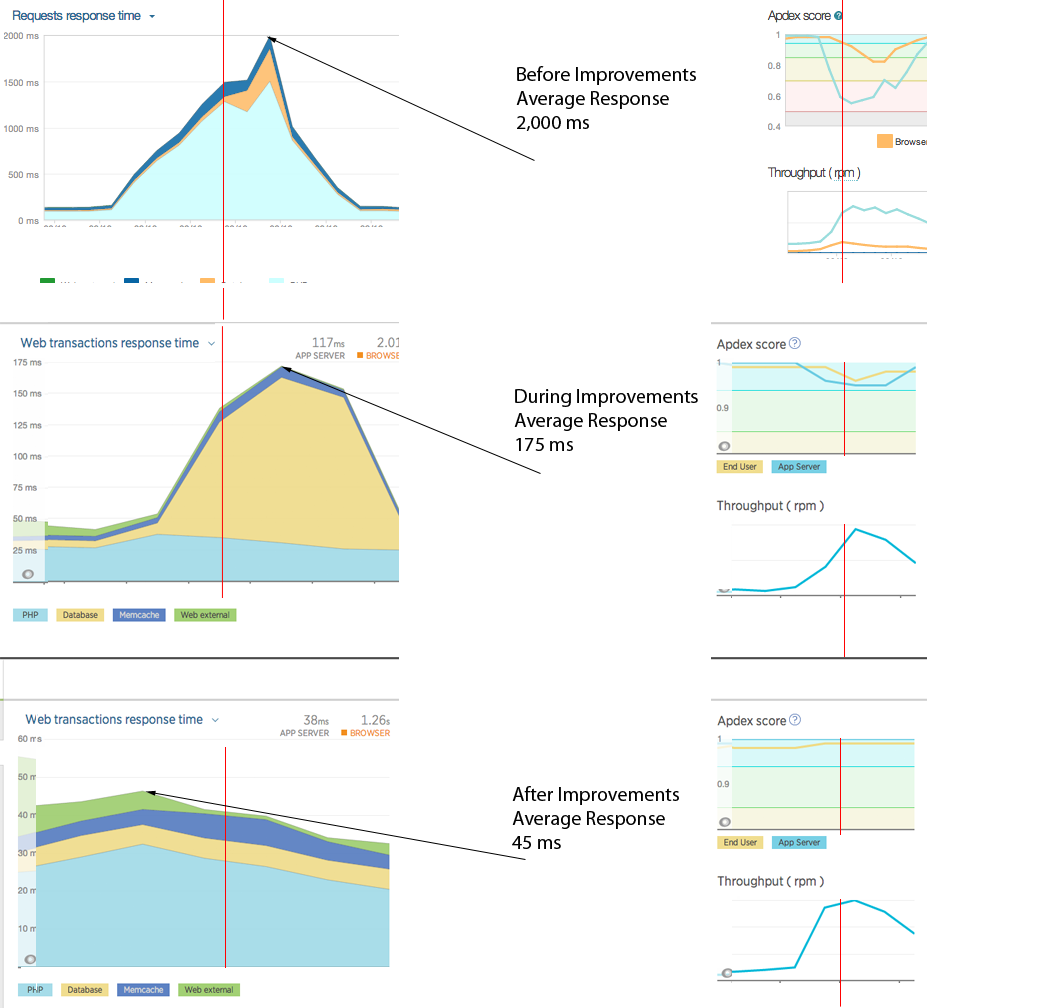
 Image generated by ChatGPT. Mistakes left as a reminder genAI is not there yet for text.
Image generated by ChatGPT. Mistakes left as a reminder genAI is not there yet for text.